20 Digital Forensics Facts for Attorneys
copyright 2025 Steve Burgess
- Deleted ≠ gone: Most deleted files remain recoverable until overwritten.
- Every case is a data case:
 Even “non-digital” disputes usually contain text messages, emails, or documents.
Even “non-digital” disputes usually contain text messages, emails, or documents. - Forensic imaging: A “bit-for-bit” or forensic working copy preserves evidence without altering the original.
- Chain of custody: In many cases, essential to maintain evidentiary integrity and courtroom admissibility.
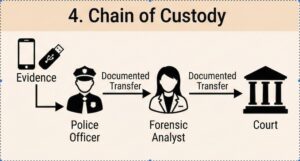
.
- Metadata matters: Creation dates, edits, GPS tags, author information, and other metadata often expose truth.

- Timestamps can shift: System clock errors or time-zone changes can mislead investigators.
- Mobile devices: Contain texts, call logs, app data, health data, photos, and location trails.
- Cloud & social media: Require proper authentication; screenshots alone are weak evidence.
- Encryption & passwords: Legal access may require subpoenas or warrants; never guess or force.
- Spoliation risk: Even good-faith access or copying can alter metadata; always image first.
- File format forensics: Different file types (PDF, DOCX, JPEG) embed distinct hidden data.
- Logs tell stories: System, email, and access logs can reconstruct user actions – and possibly reveal unauthorized access.
- Emails are not always what they seem: Headers reveal routing and spoofing attempts.
- Video & photo forensics: Compression artifacts, error levels, and metadata help expose tampering.
- Expert reports: Should clearly document tools, hashes, and methodology for repeatability.
- Hash values: Digital “fingerprints” that confirm evidence integrity (MD5, SHA-1, SHA-256).
- Forensic duplicators: Hardware tools create certified copies with built-in write blockers.
- Legal collaboration: Early involvement of forensic experts reduces spoliation and increases admissibility.
- Everything starts with data of some sort: computer, phone, tablet, email, documents.
